Toymail Talkie Network Services
Written 2018-03-31
Tags:Toymail WiFi ElectricImp
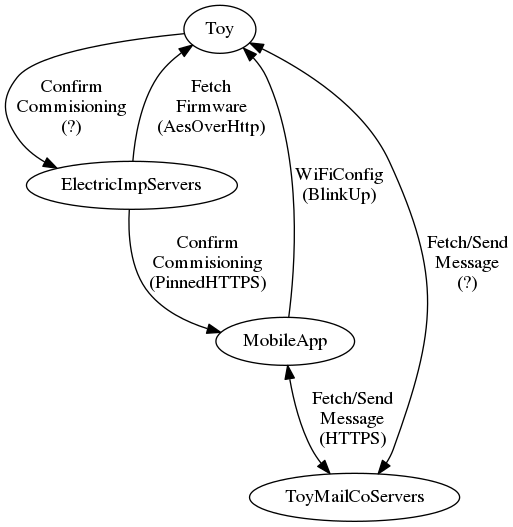
Toymail makes some pretty neat little IoT toys that let kids and parents send short voice clips to each other, or to other friends. @that_guy_ego recently brought on to SecKC to play with. I downloaded the Android APK and started disassembling it. Of note, the toys heavily leverage a technlogy from ElectricImp, which makes small IoT modules with WiFi. These are known as Imps. The Imp chip forms the majority of complexity inside the Toymail toys. Toymail runs an app on the Imp that implements the toy's behaviours and features.
Commissioning
During mobile app setup, the user is prompted for a wifi network and password. This is sent using ElectricImp's BlinkUp protocol. BlinkUp works like a simple modem, but instead of encoding data in sound, the setup information is encoded with light using the mobile device screen. Of note, the data flow is only to the toy, there's no response back. In addition to the WiFi network credentials, a unique token is generated and sent to the device. Once the toy connects to the network, it uploads the token, informing ElectricImp that it has a network connection, and ElectricImp informs the mobile app that the toy is now online.
The details of the BlinkUp protocol may be a future post
Firmware Updates
Firmware updates are served from upgrades.electricimp.com, and appear to be encrypted. We haven't yet verified this, but I'm not surprised.Imp->ElectricImp Communications
Each model of Imp uses a different DNS name to call home. For example:
- https://imp02b.boxen.electricimp.com
- https://imp07b.boxen.electricimp.com
- https://imp10a.boxen.electricimp.com
- https://imp12a.boxen.electricimp.com
Interestingly, all of the above URLs require TLS client authentication. From Petasense, who also uses Imp modules, we see that they're used to identify each client to the server.
App->Toymail Communications
Interestingly, the Android app does not use TLS pinning, and instead relies upon the mobile platform to handle security.
The following shell script will dump the possible API endpoints once the app is disassembled:
grep -r https . | cut -d "\"" -f 2 | sort -u
into:
- https://api.toymailco.com/forgot_pass
- https://api.toymailco.com/friends/
- https://api.toymailco.com/friends/accept
- https://api.toymailco.com/friends/add
- https://api.toymailco.com/friends/reject
- https://api.toymailco.com/friends/remove
- https://api.toymailco.com/friends/requests
- https://api.toymailco.com/kids
- https://api.toymailco.com/kids/ageCategory
- https://api.toymailco.com/kids/create
- https://api.toymailco.com/kids/record
- https://api.toymailco.com/kids/remove
- https://api.toymailco.com/kids/set_photo
- https://api.toymailco.com/kids/subscribe
- https://api.toymailco.com/kids?type=
- https://api.toymailco.com/kids/unsubscribe_all
- https://api.toymailco.com/message/appmailbox
- https://api.toymailco.com/message/create
- https://api.toymailco.com/message/mark_as_old_message
- https://api.toymailco.com/settings/age
- https://api.toymailco.com/settings/email
- https://api.toymailco.com/settings/password
- https://api.toymailco.com/signin
- https://api.toymailco.com/signup
- https://api.toymailco.com/support/
- https://api.toymailco.com/toys
- https://api.toymailco.com/toys/create
- https://api.toymailco.com/user/info
- https://api.toymailco.com/user/invite
- https://api.toymailco.com/user/logout
- https://api.toymailco.com/user/photo
- https://api.toymailco.com/user/profile
- https://api.toymailco.com/users/
- https://api.toymailco.com/users/?name=
Future Work
- Examine traffic between Toymail Imp and Toymail servers.
- Implement BlinkUp protocol.